NetSpyGlass vastly reduces the amount of toil for operators to monitor the network. We have unlimited programming possibilities for business level-monitoring and alerting We have gone from exerting a lot of effort with very little business impact to very little effort having a large business impact.
-Dropbox
NetSpyGlass Network Performance Monitoring
All of the capabilities that you would expect and a few that you don’t
Explore the platform
Digital Transformation
The NetSpyGlass platform provides the NetOps 2.0 foundation needed to enable digital transformation, dynamic networks and resilience.
Network Programmability
NetSpyGlass offers full custom monitoring and alerting, as well as the embedding of business-specific logic in the workflow.
Device-Level Visibility
We offer complete multi-vendor device coverage for a wide range of applications including SD-WAN, firewalls, load balancers, voice, wireless and more.
Scalability
We can manage thousands of devices, hundreds of thousands of interfaces and millions of metrics per second.
Network Automation
All variables and alerts are fully programmable and can perform functions automatically like troubleshooting.
Business Insight
The NetSpyGlass platform is capable of delivering insight to the business based on complex business logic and time-series telemetry data.
NetSpyglass
360° network view
NetSpyGlass service is the only complete and customizable solution that ensures the highest level of network availability and helps customers meet or beat their committed service levels.
Big brands trust NetSpyglass
NetSpyGlass has given us the monitoring and visibility we never had earlier. Other tools available in the market didn’t scale when we are talking about diverse network elements of 35k+ devices.
The programmability aspect allows us to have custom metrics and makes slicing and dicing data for presentations invaluable.
Built by operators for operators
Cloud-Based Platform
Runs on popular clouds like AWS & Azure.
Linux Based Agent
A linux-based agent which deploys within your infrastructure from a Web browser.
No Dedicated Hardware
Debian and CentOS-based Linux and can be hosted on a virtual machine (VM) or a shared machine and does not require dedicated hardware.
Broad Device Support
NetSpyGlass supports common vendors such as: A10, Arista, APC, Brocade, Cisco, Cumulus, Dell, F5, Force 10, HP Networking, Juniper, or any networking and security device that generates SNMP traffic.
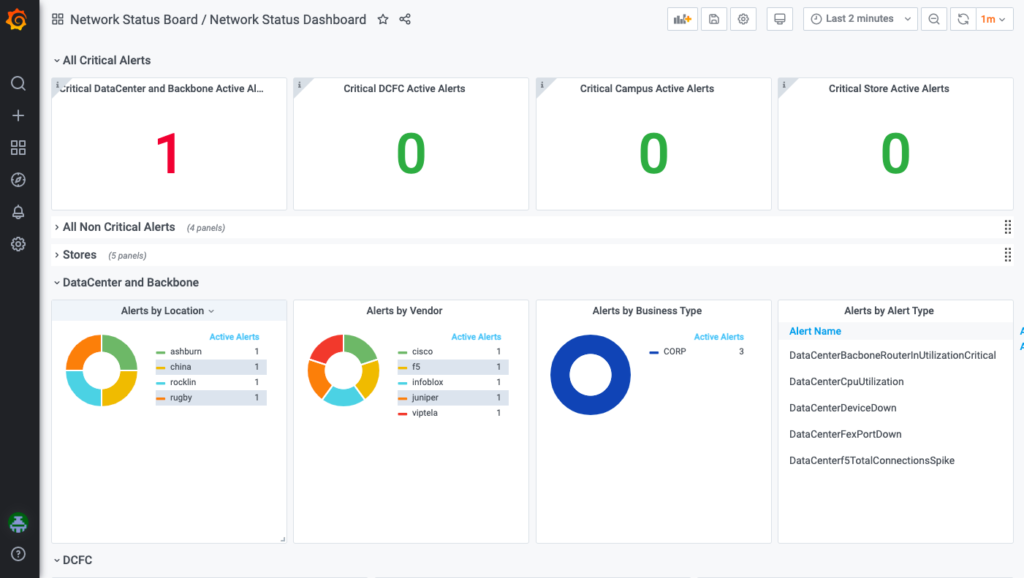
Solve difficult problems
Automate Performance Monitoring
NetSpyGlass offers automation at scale for the enterprise network— fully automating all major data gathering, processing, storage and reporting.
Cure Alert Fatigue
NetSpyGlass allows you to customize alerts to raise issues only for the alerts that impact your business goals, saving time and reducing load on your system.
Simplify Network Operations
NetSpyGlass can ingest multiple network telemetry sources to get the job done without human supervision.
Copyright © 2024. All right reserved.
